DEF CON 22 - Jim Denaro and Tod Beardsley - How to Disclose an Exploit Without Getting in Trouble |

|
|
Slides Here: https://www.defcon.org/images/defcon-22/dc-22-presentations/Denaro-Beardsley/DEFCON-22-Jim-Denaro-Tod-Beardsley-How-to-Disclose-and-Exploit-UPDATED.pdf
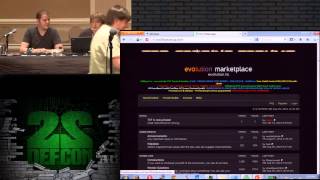
How to Disclose an Exploit Without Getting in Trouble Jim Denaro CIPHERLAW Tod Beardsley ENGINEERING MANAGER, METASPLOIT PROJECT You have identified a vulnerability and may have developed an exploit. What should you do with it? You might consider going to the vendor, blogging about it, or selling it. There are risks in each of these options. This session will cover the risks to security researchers involved in publishing or selling information that details the operation of hacks, exploits, vulnerabilities and other techniques. This session will provide practical advice on how to reduce the risk of legal action and suggest several approaches to responsible disclosure. Jim Denaro (@CipherLaw) is the founder of CipherLaw, a Washington, D.C.-based consultancy and focuses his practice on the legal, technical, and ethical issues faced by innovators in information security. Jim is a frequent speaker and writer on legal issues in information security and has experience in a wide range of technologies, including intrusion detection and prevention, botnet investigation, malware discovery and remediation, and cryptography. Jim is a regular consultant on responsible disclosure policies and is involved in programs to shield researchers who disclose responsibly. Jim has completed professional coursework at MIT and Stanford in computer security and cryptography. He also holds technical certifications from the Cloud Security Alliance (CCSK) and Cisco Systems (CCENT), and has passed the CISSP examination (pending certification). Before becoming an attorney, Jim spent obscene amounts of time looking at PPC assembly in MacsBug. Tod Beardsley (@todb) is engineering manager for the open source Metasploit project, as well as one of the core developers on the framework. His background is primarily in intrusion prevention, vulnerability assessment and identification, anti-fraud/anti-phishing countermeasures, penetration testing and compliance auditing, intrusion detection and response, protocol analysis, and host hardening. He is also interested in computer crime forensics and recovery, reverse engineering and binary analysis, steganographic communication channels, and cryptography in general. Tod’s technical specialties include protocol analysis and reverse engineering, intrusion detection and prevention, phishing and online fraud, open source software engineering collaboration, and application vulnerability research and exploitation. |