The Evolution of Network Protocol Architecture |

|
|
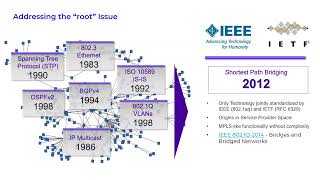
Interestingly, many organizations will 'refresh' or 'modernize' their networks with shiny new switches with updated speeds and feeds. Yet many times, protocols are implemented, which were ratified in the late 1980s and early 1990s. When we look at 'modernizing' a network infrastructure, we need to look past the switches and start to examine the protocol architectures and their evolution over time. There will be a particular focus on the concept of network fabrics and exactly what they are all about and what they attempt to accomplish. Learn more in this video with Distinguished Principal Engineer Ed Koehler.
To learn more, please visit - https://www.extremenetworks.com/extreme-networks-blog/aspects-of-trust-in-technology-human-society/ |